环境
工具: Palera1n (A8 ~ A11)
设备: iPhone 8 (A11) 、iOS 16.7.10
越狱
无根越狱: palera1n -l (rootless)
有根越狱: palera1n -f (rootful)
这里我们使用有根越狱: palera1n -f (rootful) 的方式
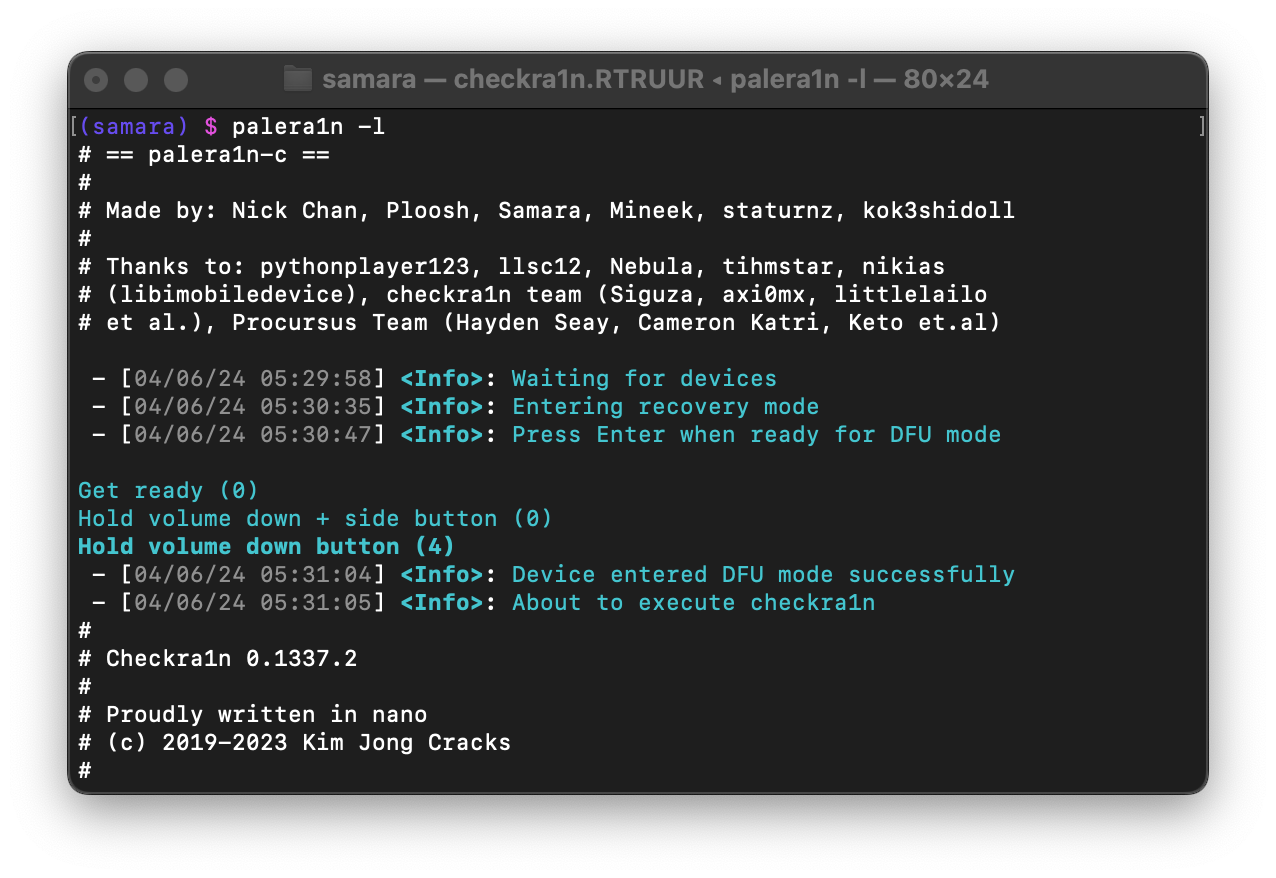
创建有根越狱 fakeFS 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 $ palera1n -f -c - [12/18/24 14:11:14] <Info>: Waiting for devices - [12/18/24 14:11:15] <Info>: Entering recovery mode - [12/18/24 14:11:25] <Info>: Press Enter when ready for DFU mode Hold volume down + side button (0) Hold volume down button (3) - [12/18/24 14:11:39] <Info>: Device entered DFU mode successfully - [12/18/24 14:11:40] <Info>: About to execute checkra1n - [12/18/24 14:11:40] <Verbose>: Starting thread for Apple TV 4K Advanced board - [12/18/24 14:11:40] <Info>: Waiting for DFU mode devices - [12/18/24 14:11:43] <Verbose>: DFU mode device found - [12/18/24 14:11:43] <Info>: Checking if device is ready - [12/18/24 14:11:43] <Verbose>: Attempting to perform checkm8 on 8015 11 - [12/18/24 14:11:43] <Info>: Setting up the exploit - [12/18/24 14:11:43] <Verbose>: == checkm8 setup stage == - [12/18/24 14:11:43] <Verbose>: Entered initial checkm8 state after 1 steps - [12/18/24 14:11:44] <Verbose>: Stalled input endpoint after 3084 steps - [12/18/24 14:11:45] <Verbose>: DFU mode device disconnected - [12/18/24 14:11:45] <Verbose>: DFU mode device found - [12/18/24 14:11:45] <Verbose>: == checkm8 trigger stage == - [12/18/24 14:11:45] <Info>: Checkmate! - [12/18/24 14:11:45] <Verbose>: Device should now reconnect in download mode - [12/18/24 14:11:45] <Verbose>: DFU mode device disconnected - [12/18/24 14:11:51] <Info>: Entered download mode - [12/18/24 14:11:51] <Verbose>: Download mode device found - [12/18/24 14:11:51] <Info>: Booting PongoOS... - [12/18/24 14:11:53] <Info>: Found PongoOS USB Device - [12/18/24 14:11:54] <Info>: Booting Kernel... - [12/18/24 14:11:54] <Info>: Please wait up to 10 minutes for the fakefs to be created. - [12/18/24 14:11:54] <Info>: Once the device reboots into recovery mode, run again without the -c (Create FakeFS) option to jailbreak.
有根越狱 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 $ palera1n -f - [12/18/24 14:19:18] <Info>: Waiting for devices - [12/18/24 14:19:19] <Info>: Press Enter when ready for DFU mode Hold volume down + side button (0) Hold volume down button (3) - [12/18/24 14:19:37] <Info>: Device entered DFU mode successfully - [12/18/24 14:19:37] <Info>: About to execute checkra1n - [12/18/24 14:19:38] <Verbose>: Starting thread for Apple TV 4K Advanced board - [12/18/24 14:19:38] <Info>: Waiting for DFU mode devices - [12/18/24 14:19:42] <Verbose>: DFU mode device found - [12/18/24 14:19:42] <Info>: Checking if device is ready - [12/18/24 14:19:42] <Verbose>: Attempting to perform checkm8 on 8015 11 - [12/18/24 14:19:42] <Info>: Setting up the exploit - [12/18/24 14:19:42] <Verbose>: == checkm8 setup stage == - [12/18/24 14:19:42] <Verbose>: Entered initial checkm8 state after 1 steps - [12/18/24 14:19:42] <Verbose>: Stalled input endpoint after 439 steps - [12/18/24 14:19:42] <Verbose>: DFU mode device disconnected - [12/18/24 14:19:42] <Verbose>: DFU mode device found - [12/18/24 14:19:42] <Verbose>: == checkm8 trigger stage == - [12/18/24 14:19:42] <Info>: Checkmate! - [12/18/24 14:19:42] <Verbose>: Device should now reconnect in download mode - [12/18/24 14:19:42] <Verbose>: DFU mode device disconnected - [12/18/24 14:19:49] <Info>: Entered download mode - [12/18/24 14:19:49] <Verbose>: Download mode device found - [12/18/24 14:19:49] <Info>: Booting PongoOS... - [12/18/24 14:19:51] <Info>: Found PongoOS USB Device - [12/18/24 14:19:51] <Info>: Booting Kernel...
安装市场和必要插件
越狱完成后,成功进入系统会显示Palera1n的开机画面
进入SpringBoard后,会有palera1n的图标 加载出现(最后一个图标)
满足以上两点,代表越狱流程顺利完成
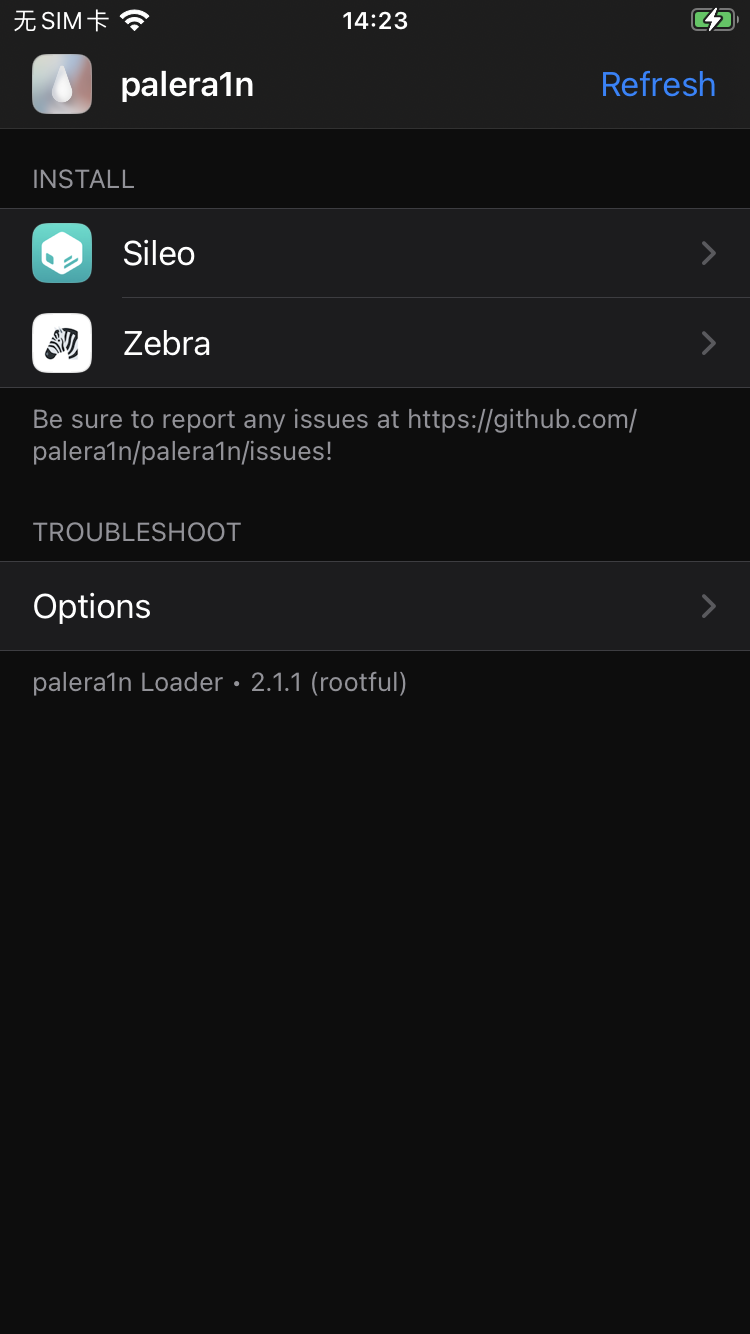
① 点击进入palera1n应用
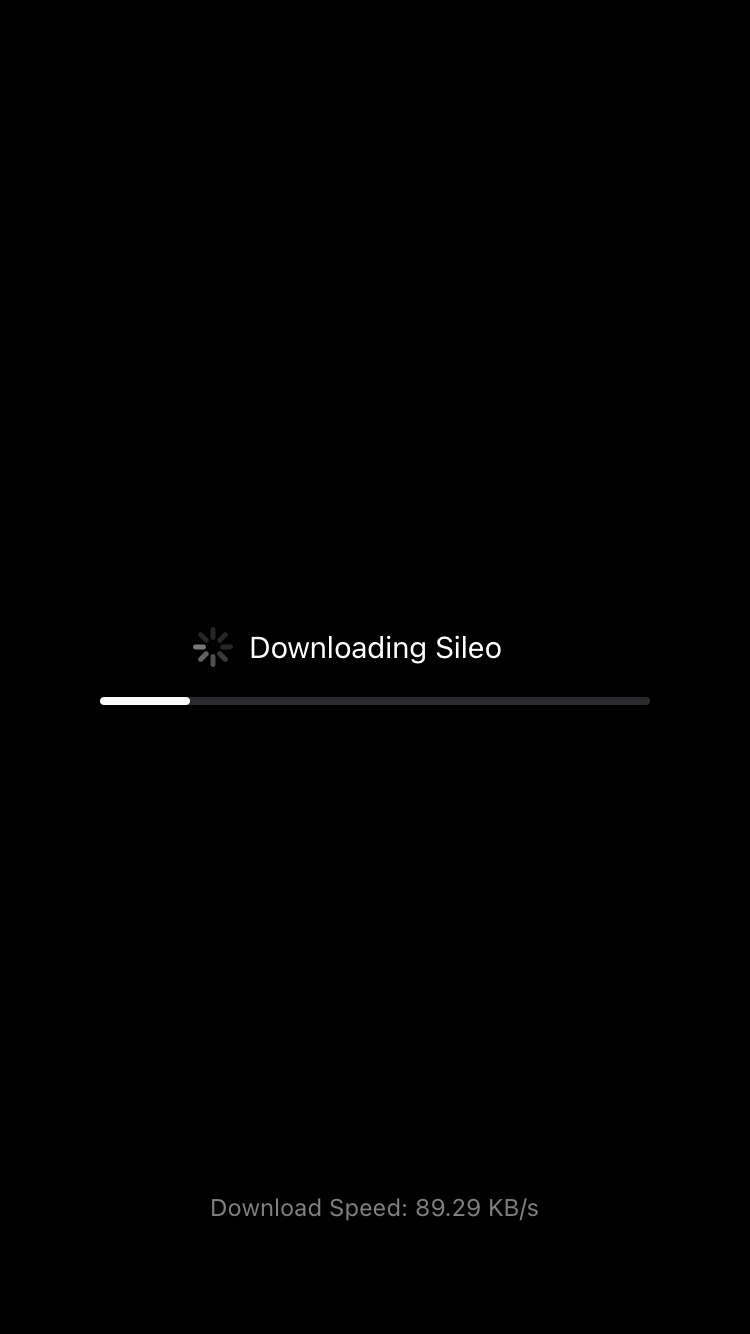
② 点击Sileo,安装市场
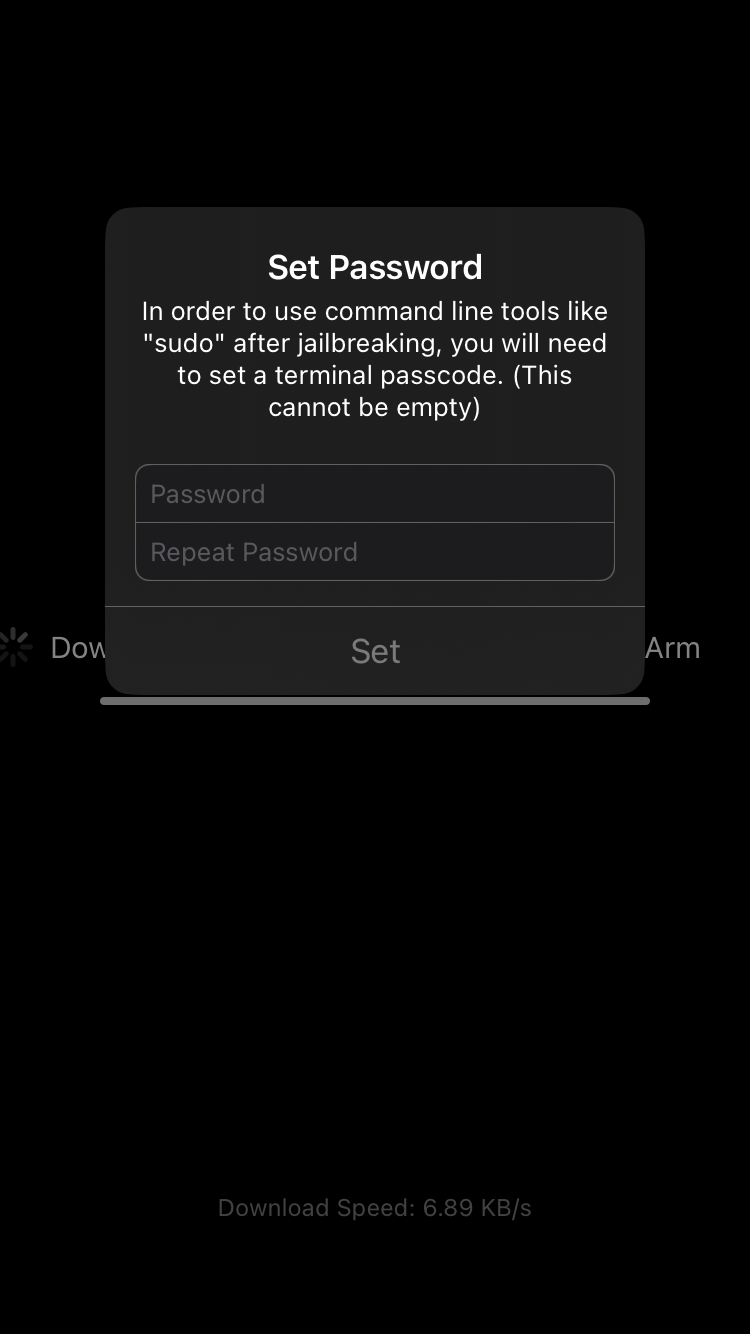
③ 设置SSH, mobile默认密码
④ Sileo市场安装成功
⑤ 进入Sileo市场, 安装好以下几个基本必要的插件
openssh (SSH访问到iPhone设备内部)
Ellekit (所有运行插件的基础库)
Appsync (绕过app的证书签名校验)
修改SSH密码 通过上面设置的mobile用户SSH进入手机内部
1 2 $ ssh mobile@192.168.1.105 (mobile@192.168.1.105) Password for mobile@iPhone:
修改root用户的密码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 $ sudo passwd root We trust you have received the usual lecture from the local System Administrator. It usually boils down to these three things: For security reasons, the password you type will not be visible. [meow] password for mobile: Changing password for root. Old Password: New Password: Retype New Password:
切换到root用户下,验证当前用户是否是root
1 2 3 4 $ sudo su iPhone:/private/var/mobile root# whoami root iPhone:/private/var/mobile root#
至此,我们在iPhone 8 (iOS 16)设备越狱环境基本上配置完成,可以完成后续的各种逆向和DIY等玩法了
越狱完成,如果我们想恢复到原始系统,那么就要移除越狱
移除越狱 以Rootful有根越狱为例
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 $ palera1n -f --force-revert - [12/19/24 08:44:11] <Info>: Waiting for devices - [12/19/24 08:44:11] <Info>: Entering recovery mode - [12/19/24 08:44:22] <Info>: Press Enter when ready for DFU mode Hold volume down + side button (0) Hold volume down button (4) - [12/19/24 08:44:37] <Info>: Device entered DFU mode successfully - [12/19/24 08:44:37] <Info>: About to execute checkra1n - [12/19/24 08:44:38] <Verbose>: Starting thread for Apple TV 4K Advanced board - [12/19/24 08:44:38] <Info>: Waiting for DFU mode devices - [12/19/24 08:44:42] <Verbose>: DFU mode device found - [12/19/24 08:44:42] <Info>: Checking if device is ready - [12/19/24 08:44:42] <Verbose>: Attempting to perform checkm8 on 8015 11 - [12/19/24 08:44:42] <Info>: Setting up the exploit - [12/19/24 08:44:42] <Verbose>: == checkm8 setup stage == - [12/19/24 08:44:42] <Verbose>: Entered initial checkm8 state after 1 steps - [12/19/24 08:44:42] <Verbose>: Stalled input endpoint after 606 steps - [12/19/24 08:44:42] <Verbose>: DFU mode device disconnected - [12/19/24 08:44:42] <Verbose>: DFU mode device found - [12/19/24 08:44:42] <Verbose>: == checkm8 trigger stage == - [12/19/24 08:44:45] <Info>: Checkmate! - [12/19/24 08:44:45] <Verbose>: Device should now reconnect in download mode - [12/19/24 08:44:45] <Verbose>: DFU mode device disconnected - [12/19/24 08:44:51] <Info>: Entered download mode - [12/19/24 08:44:51] <Verbose>: Download mode device found - [12/19/24 08:44:51] <Info>: Booting PongoOS... - [12/19/24 08:44:53] <Info>: Found PongoOS USB Device - [12/19/24 08:44:53] <Info>: Booting Kernel...
重启之后进入系统,会弹窗需要再次重启移除越狱 或者进入恢复模式重新越狱
这里我们点击Reboot now , 重启设备开机看不到palera1n的开机动画 ,进入系统也没有palera1n的桌面图标
至此移除越狱成功
相关文献 本文简要的记录 iOS 16 越狱和移除越狱流程, 更多玩法或其他内容,请参阅以下文献